New research from Venafi shows complexity is due to increase as companies plan to host more than half their applications in the cloud.
Security risks higher in the cloud
Venafi today announced the findings of new research that evaluates the complexity of cloud environments and its impact on cybersecurity.
The study found that 81% of organizations have experienced a cloud-related security incident over the last 12 months, with almost half (45%) suffering at least four incidents. The underlying issue for these security incidents is the dramatic increase in security and operational complexity connected with cloud deployments.
Given that the organizations in this study currently host two fifths (41%) of their applications in the cloud but expect that percentage to grow to 57% over the next 18 months, this complexity will continue to increase. A key security control for cloud and hybrid networks is with a machine identity management control plane.
More than half (51%) of the security decision makers (SDMs) in the study believe security risks are higher in the cloud than on premises, citing several issues.

Zero Trust with cert-manager, Istio and Kubernetes
Applications highly distributed
Applications are now highly distributed and will invariably exist outside the data center, often in different cloud environments. Containers are now the primary machine context in cloud native systems, using application resources that do not need to be physically hosted in a single location.
This means container security is formulated around what development teams and operations teams regard as best practice and yet this will not always align with conventional enterprise security policy.
The most common cloud-related security incidents respondents have experienced are:
- Security incidents during runtime (34%)
- Unauthorized access (33%)
- Misconfigurations (32%)
- Major vulnerabilities that have not been remediated (24%)
- A failed audit (19%)
The critical operational and security concerns that SDMs have in relation to moving to the cloud are:
- Hijacking of accounts, services or traffic (35%)
- Malware or ransomware (31%)
- Privacy/data access issues, such as those from GDPR (31%)
- Unauthorized access (28%)
- Nation-state attacks (26%)
Machine identities ripe for targeting
"Attackers are now on board with business's shift to cloud computing," said Kevin Bocek, vice president of security strategy and threat intelligence at Venafi. “The ripest target of attack in the cloud is identity management, especially machine identities. Each of these cloud services, containers, Kubernetes clusters and microservices needs an authenticated machine identity — such as a TLS certificate — to communicate securely. If any of these identities is compromised or misconfigured, it dramatically increases security and operational risks.”
The study also investigated how responsibility for securing cloud-based applications is currently assigned across internal teams. This varies widely across organizations, with enterprise security teams (25%) the most likely to manage app security in the cloud, followed by operations teams responsible for cloud infrastructure (23%), a collaborative effort shared between multiple teams (22%), developers writing cloud applications (16%) and DevSecOps teams (10%). However, the number of security incidents indicates that none of these models are effective at reducing security incidents.
Consensus not clear on responsibility
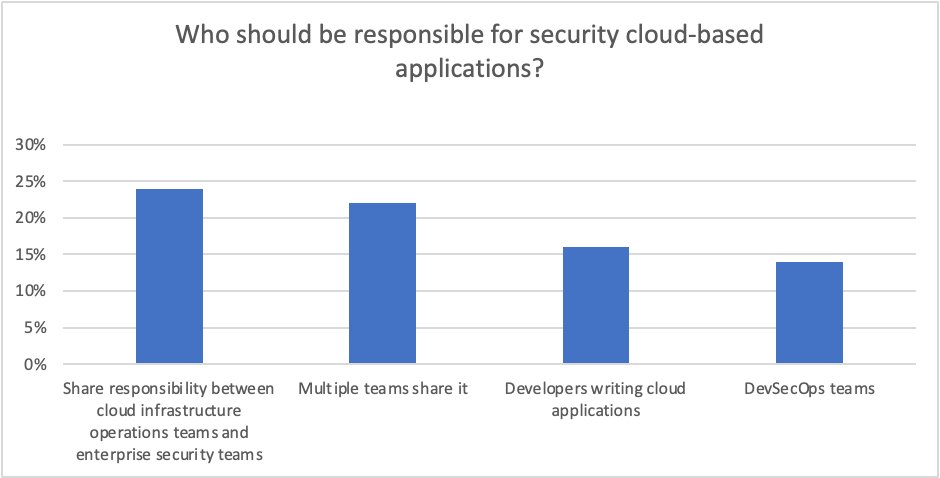
When asked who should be responsible for security cloud-based applications, again, there was still no clear consensus. The most popular option shares responsibility between cloud infrastructure operations teams and enterprise security teams (24%). The next most popular options for responsibility are having multiple teams share it (22%), developers writing cloud applications (16%) and DevSecOps teams (14%).
The challenges with shared responsibility models are that security teams and development teams have very different goals and objectives. Developers need to move fast to accelerate innovation while security teams often do not have visibility into what development teams are doing. Without this visibility security teams cannot evaluate how those controls stack up against security and governance policies.
“Security teams want to collaborate and share responsibility with the developers who are cloud experts, but all too often they’re left out of cloud security decisions,” noted Bocek. “Developers are making cloud native tooling and architecture decisions that decide approaches to security without involving security teams. And we can already see the results of that approach: Security incidents in the cloud are rapidly growing.
Continued Bocek: “We need to reset the approach to cloud security and create consistent, observable, controllable security services across clouds and applications. Architecting in a control plane for machine identity is a perfect example of a new security model created specifically for cloud computing. This approach embeds security into developer processes and allows security teams to protect the business without slowing down engineers.”
Cover every cluster with ease and efficiency.
Related Posts
- Why Zero Trust Requires Machine Identity Management
- Dynamism in the Cloud Complicates the Task of Securing Machine Communication
- 5 Machine Identity Risks You’ll Want to Avoid
- 4 Ways Machine Identities Will Challenge You
About the research
Conducted by Sapio in July 2022, Venafi’s study evaluated the opinions of 1,101 security decision makers across the United States, United Kingdom, France, Germany, Benelux (Belgium, Netherlands, Luxembourg) and Australia.

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.

![81% of Companies have had a Cloud Security Incident in the Last Year [Venafi Research] - cover graphic](/_next/image/?url=https%3A%2F%2Fcdn.venafi.com%2F994513b8-133f-0003-9fb3-9cbe4b61ffeb%2F69fa0853-86b3-4107-bacf-550a8e385d80%2Faid_field_img__6e87372fe07e6579287fbf0fd52d6575.jpg%3Fw%3D960%26h%3D540%26fm%3Dwebp%26q%3D85%26fit%3Dcrop&w=3840&q=75&dpl=dpl_CCHxY4sjzWPuuwz2oe2scS3ctPCM)