We’ve known for a long time that SSH keys are valuable to cyber criminals—for many of the same reasons that they are valuable to us. They provide authenticated access to the secure systems we need to get into. Good when we do it. Bad when people we don’t know do it. But despite the high value of SSH keys, protecting them often becomes more of an afterthought for many organizations. So when cyber criminals gain an entry point into our networks, it may be easier than you think for them to find and misuse them to pivot from machine to machine.
Just this last week, we learned that two malicious Python libraries were stealing SSH and GPG keys. Discovered on December 1 by German software developer Lukas Martini, the two malicious clone libraries were created by the same developer. They were immediately removed after dateutil developers and the PyPI security team were notified. One library had been available for only two days, but the other had been live for almost a year.

SSH Machine Identity Management for Dummies
ZDNet reported that the trojanized Python libraries used a technique called typosquatting to mimic other more popular libraries by registering similarly-looking names. “The first is ‘python3-dateutil,’ which imitated the popular ‘dateutil’ library. The second is ‘jeIlyfish’ (the first L is an I), which mimicked the ‘jellyfish’ library.”
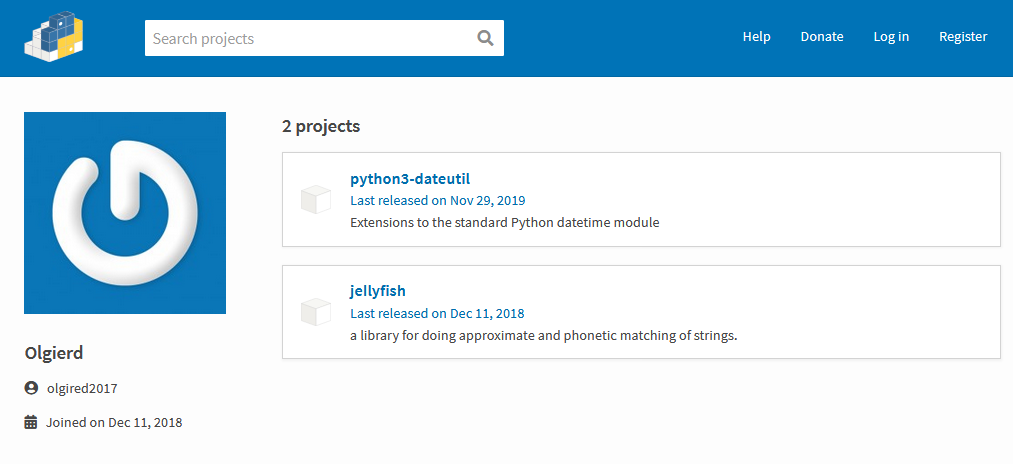
Image: ZDNet
Examining the impact
Because the malicious libraries deleted so quickly, it was initially difficult to determine what, exactly was their criminal intent. To learn more about the impact, ZDNet asked a member of the dateutil dev team, Paul Ganssle, to investigate the malicious code. According to Ganssle "The code directly in the ‘jeIlyfish’ library downloads a file called 'hashsum' that looks like nonsense from a gitlab repo, then decodes that into a Python file and executes it." He continued, "It looks like [this file] tries to exfiltrate SSH and GPG keys from a user's computer and send them to this IP address: http://68.183.212.246:32258."
Jing Xie, senior threat intelligence researcher at Venafi, warns that the growing reliance on OSLs for software development leaves many companies vulnerable to trust-based attacks. Unsuspecting developers and site managers can actively introduce malware into their own software and websites when they use a compromised OSL. When the infected code is distributed by a legitimate developer, the resulting malicious software will be automatically trusted by its users’ computers, infecting their computers and networks.
"55% increase in breaches resulting from OSL trust attacks in 2018"
“This is a very real problem, and recent research from Sonatype revealed a 55 percent increase in breaches resulting from OSL trust attacks in 2018,” said Xie. “It’s unrealistic, though, to ask businesses to completely change their practices by limiting the use of OSLs. Instead, the industry needs to work together to make open source code more dependable.”
Since trust-based attacks can infect millions of computers very quickly, it is critical that organizations increase their awareness about the risks associated with OSL security. The Developer hub recommends that, “All developers are advised to check if they’ve accidentally downloaded or imported the malicious libraries rather than the originals. If so, it’s advisable to change all SSH and GPG keys used over the past year.”
Jing Xie explains the dangers of open source libraries, and why the development community is just starting to take notice.
Get a FREE & Confidential SSH Risk Assessment from Venafi!
Related posts

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.

![Are Cyber Criminals Targeting Your SSH Keys? [in Python Libraries] - cover graphic](/_next/image/?url=https%3A%2F%2Fcdn.venafi.com%2F994513b8-133f-0003-9fb3-9cbe4b61ffeb%2F6f4ce845-e593-4d37-a349-471cea7f915c%2Faid_field_img__8e95544a3b6bb2a1966e12d9bb32a8ce.png%3Fw%3D960%26h%3D540%26fm%3Dwebp%26q%3D85%26fit%3Dcrop&w=3840&q=75&dpl=dpl_CCHxY4sjzWPuuwz2oe2scS3ctPCM)