All enterprises rely on Secure Shell (SSH) keys to authenticate privileged users and establish trusted access to critical systems, including application servers, routers, firewalls, virtual machines, cloud instances, and many other devices and systems. SSH keys are used for privileged administrative operations by system administrators, but are also used for secure machine-to-machine automation of critical business functions. Once SSH keys are put in place to enable client authentication, they enable ongoing, automatic connections from one system to another, without needing to enter a password.
What is SSH?
SSH is a cryptographic network protocol that gives users a secure way to access a computer over an unsecured network. To be clear, SSH is a short way of referring to Secure Shell or Secure Socket Shell. But it can also refer to the suite of utilities that implement the SSH protocol.
Administrators use SSH to log in to another computer over a network, execute commands and move files between computers. In addition to providing this level of secure access, SSH can automate processes such as file transfers, issue remote commands, and manage network infrastructure. To do all of that securely, SSH provides strong password and public key authentication to enable encrypted data communications between two computers.
SSH uses a client-server model to connect an SSH client application with an SSH server to run a session. A single session requires one public key pair to authenticate the remote machine to the local machine and another to authenticate the local machine to the remote machine.
For example, in a terminal session SSH employs a user ID to allow the client to connect to a server. The first time a connection between the client and server is negotiated, the user must provide the remote host's public key to connect. Once that host key is stored in the system’s hidden directory, the client system can authenticate to that server again without any further approvals.
SSH plays a pivotal roles in machine identity management, as it does more than authenticate over an encrypted connection. SSH ensures that all traffic is encrypted, keeping actions private whether administrators are transferring a file or running a command.

SSH Machine Identity Management for Dummies
How does SSH work?
Secure Shell (SSH) keys operate within a network protocol designed to securely connect two entities through advanced cryptographic methods. SSH keys authenticate the parties and enable them to exchange commands and responses via a variety of data handling techniques. SSH keys use a symmetric encryption system, such as AES, Blowfish, 3DES, CAST128, or Arcfour, to encrypt the entire session, ensuring data confidentiality. Asymmetric encryption, on the other hand, is utilized during the initial exchange process to establish the symmetric encryption and to authenticate via keys. Additionally, SSH employs hash-based message authentication codes (HMACs) to verify the integrity of each received message, ensuring data hasn't been tampered with during transmission. Thus, SSH keys play a pivotal role in maintaining a secure and reliable communication channel
As Justin Elingwood of DigitalOcean explains, SSH encrypts data exchanged between two parties using a client-server model. The server listens to a designated port for connections, while the client is responsible for the Transmission Control Protocol (TCP) handshake with the server. That initial connection sets the stage for the server and client negotiating the encryption of the session based upon what protocols they support. To negotiate a session key, both parties use a version of the Diffie-Hellman algorithm to create a private key via an agreed upon seed value and encryption generator (such as AES) as well as a public key. Their private key, the other party's public key, and the seed value form the basis for the shared secret key, a symmetric secret which encrypts the rest of the connection.
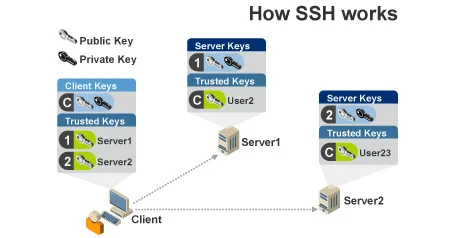
Once the parties have played an equal role in generating the shared secret key, they must authenticate themselves. The most common means of authentication is via SSH asymmetric key pairs. The server uses the public key to encrypt a message and send it to the client. If the client has the correct private key, they can decrypt the message and send it back to the server for verification.
What is the newest version of SSH?
As of this writing, the SSH protocol comes in two versions. The first version uses private RSA keys to decrypt challenges encrypted with the corresponding public key. But SSH protocol version 1 is limited in its support of message authorization codes, compression algorithms, and the algorithms necessary for key exchanges. By comparison, Version 2 of the protocol requires that the client sign a message and transmit the signature (not the message) with the public key used. The server then recreates the message and verifies the server. SSH version 2 is also not a monolithic protocol.
The newest version is made up of a series of protocols that include improved public key certification, encryption standards, and even support for public key certificates.
In both versions, SSH keys serve a crucial function in protecting the involved parties' information. It's therefore in organizations' interest to manage their SSH keys. That process involves safeguarding the keys that should be trusted and blocking those that shouldn't.
Enterprise organizations have thousands of SSH connections — each one with the potential to lead to a security breach if not protected. Make sure you know where your SSH keys are stored to avoid failing SSH audits and costly fines. Download this brief to learn how your organization can reduce SSH risks.
(This post has been updated. It was originally published on February 5, 2019.)
Get a FREE & Confidential SSH Risk Assessment from Venafi!
Related blogs

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.

