Newly released emails corroborate the forensic analysis conducted by Venafi TrustNet certificate reputation service which concluded that Secretary of State Hillary Clinton did not use encryption on her email server at the beginning of her term.
Earlier this year, Venafi threat intelligence identified that the email server operated for Secretary Clinton and mail.clintonemail.com appeared not to use encryption for the first 3 months of operation—leaving her email and server potentially open to hackers. During this vulnerable period without encryption, Secretary Clinton travelled to China, Egypt, Israel, South Korea, and other locations outside of the U.S.
Venafi threat intelligence identified the first digital certificate issued for the server was on 29 March 2009 while Secretary Clinton was sworn in to office on 22 January 2009 and the clintonemail.com domain was registered on 13 January 2009. If the server did not use encryption, access using browsers, smartphones, and computers could have been compromised with man-in-the middle (MITM) attacks, allowing communications to be monitored. These attacks could have allowed for emails or login credentials to be captured, leading to further long-term access to Secretary Clinton’s email and calendar by adversaries.
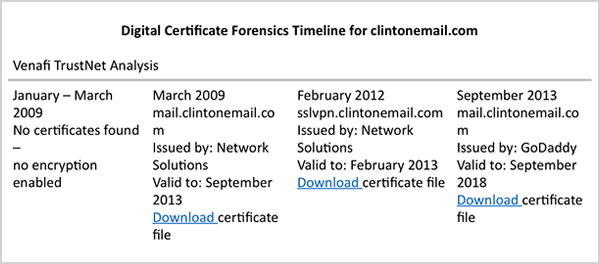
First clintonemail.com digital certificate obtained in 2009 from Network Solutions.

But over the past few months, one question continued to linger for the Venafi research team and others in the security community: Did Secretary Clinton actually use the email server during the time a digital certificate was not in use and encryption was not enabled?
With the public release of additional clintonemail.com messages, Venafi now believes it can definitively answer this question: Yes, Secretary Clinton did use the clintonemail.com server to send and receive messages while the server did not have a digital certificate installed and was not using encryption.
Email Server Use Timeline
- Wednesday, 18 March 2009—the date of the earliest message publicly released that was sent to Secretary Clinton at clintonemail.com.
- Saturday, 21 March 2009—the earliest date that publicly-available email messages show the Secretary using the email address, hdr22@clintonemail.com, to send messages.
- Sunday, 29 March 2009—the date the first digital certificate for mail.clintonemail.com was acquired by Justin Cooper.
The first publicly-known email to be sent by Secretary Clinton using clintonemail.com is on Saturday, 21 March 2009.
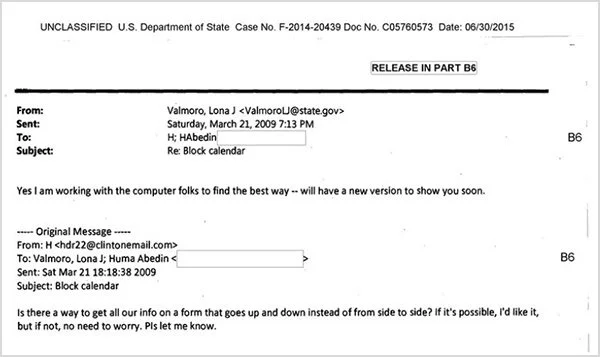
Venafi cannot confirm if earlier emails exist or will be made publicly available. Therefore, for at least 11 days, Venafi concludes that while in use the server did not use encryption for access by browsers, smartphones, and computers. The email sent to Secretary Clinton on 18 March is from someone outside of the State Department. This may indicate the email address was in use and known publicly before 18 March. Only public release of further emails by the State Department can confirm this. After 29 March and until the server was taken offline in 2015, the server did operate with a valid digital certificate and did use encryption for browser, smartphone, and computer access.
Venafi also identified that the mail.clintonemail.com server was operating Microsoft’s Outlook Web Access (OWA) in March 2015, meaning that access was possible not just with a smartphone or desktop application like Outlook, but using any web browser. While OWA is installed by default with Microsoft Exchange and the server was hosting the application with Microsoft IIS 7 (released by Microsoft in February 2008), Venafi cannot confirm when web browser access with Outlook Web Access was first enabled.
Outlook Web Access in use and accessible from any browser for mail.clintonemail.com in March 2015 (first date of use cannot be confirmed by Venafi).
The following digital certificate forensic analysis was documented by Venafi in March 2015 to understand when encryption was used on mail.clintonemail.com. Get the full analysis.
What are your thoughts about Secretary Clinton’s use of her email server before encryption was enabled?

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.

