Fraudsters launched a new phishing campaign in which they are using TLS certificates in an attempt to steal Netflix users’ account credentials.
Dr. Johannes B. Ullrich, Dean of Research at SANS Technology Institute, received a sample of the campaign on 19 June. The email was in his words the “weak part of this exploit.” He based his conclusion on the fact that the email was labeled as spam and that its body content was full of grammatical mistakes.
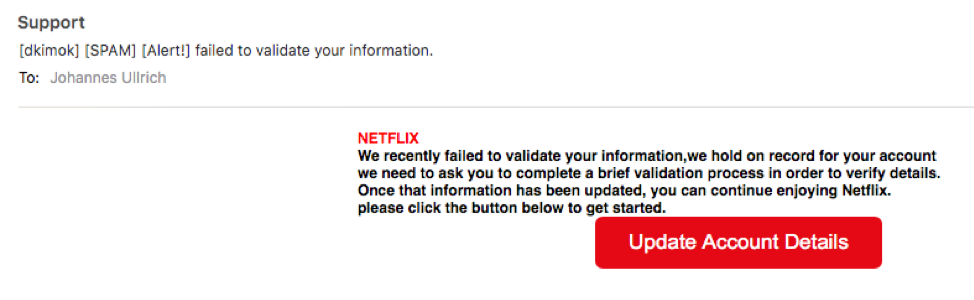
We recently failed to validate your information,we hold on record for your account we need to ask you to complete a brief validation process in order to verify details. Once that information has been updated, you can continue enjoying Netflix. Please click the button below to get started.
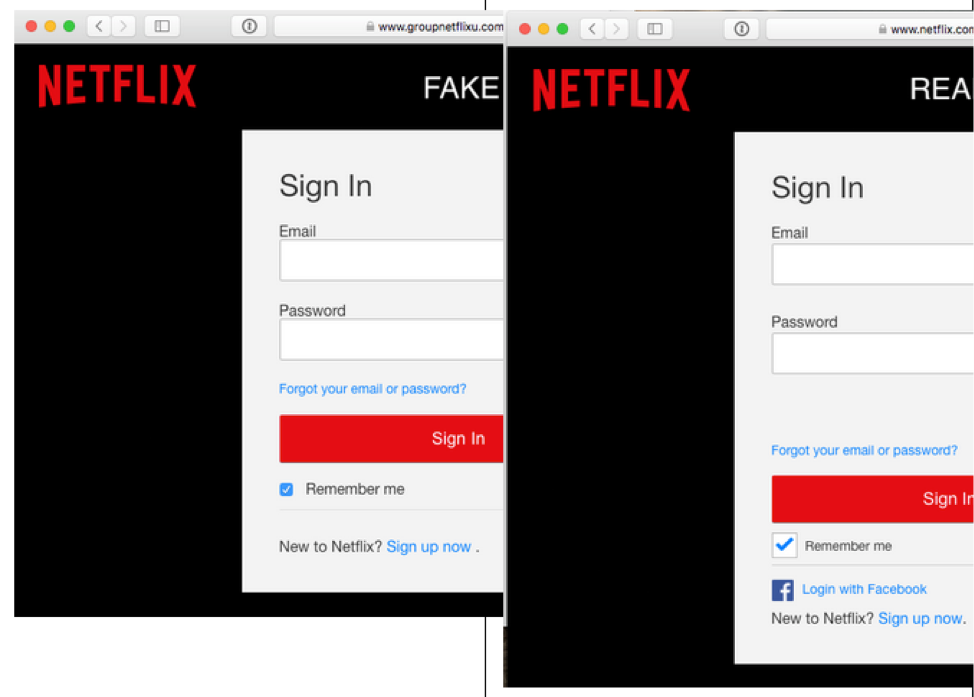
Though error-ridden, the attack email provided crucial insight into the rest of the phishing campaign. Dr. Ulrich used the message to trace the attack’s beginning to a compromised site running CMS software like WordPress or Drupal and likely suffering from an unpatched plugin or a weak admin password. He also determined that those responsible for the campaign purchased a TLS certificate for a Netflix-related hostname like “netflix.login.domain.com” or a similar domain used in the phish. All of this in an attempt to trick users into visiting a malicious website designed to look similar to the real Netflix login page. So similar, in fact, that the only apparent differentiating factor was the option for users to authenticate themselves via Facebook on the legitimate sign-in site.
It’s not particularly surprising that those behind the campaign chose to use TLS. The use of encryption among attackers is on the rise. In 2017, Zscaler blocked an average of 12,000 phishing attempts using SSL/TLS per day. This figure marked an increase of 400 percent over the traffic it blocked 2016.

SSL/TLS Certificates and Their Prevalence on the Dark Web
Even so, Dr. Ulrich thought that the phisher made a mistake by using TLS in an attempt to piggyback off legitimate Netflix members’ accounts. As he explained in a blog post:
"I found the sites pretty easily via certificate transparency logs, and I think Netflix, or someone else, is doing the same thing as I saw these sites often labeled as "deceptive" by Google's safe browsing feature, before the phishing part of the site was life. I doubt many users would notice if the site didn't use TLS."
Certificate transparency logs are useful in that they help keep track of digital certificates. It’s therefore no wonder Google issued a mandate for its Chrome browser requiring that all newly issued TLS certificate authorities comply with the Chromium Certificate Transparency (CT) Policy, as researchers like Dr. Ulrich can use CT logs to investigate instances where someone might be misusing a certificate.
Organizations need to make sure they monitor their digital certificates for signs of misuse. To do that, they need to obtain complete visibility over their certificates. Learn how Venafi can help.
Get a 30 Day Free Trial of TLS Protect Cloud, Automated Certificate Management.
Related posts

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.

