What does Privacy mean within your organization? How much privacy does an organization need? Should you even have a privacy function?
There isn’t a shortage of definitions on what ‘Privacy’ means. I did a quick google search on the key words “Privacy Definition” and it returned 173,000,000 results. Why isn’t there a single simple interpretation? Suppose I had a discussion with a broader group of privacy professionals and during our conversation I asked each of them what their definition or interpretation of privacy is? Do you think these ‘experts’ would agree on a single interpretation? Highly unlikely. Why not?
There are actually a number of definitions and dimensions to privacy. It is not my intent to debate those perspectives in this post. I just want to illustrate that privacy is complicated, the privacy profession is sophisticated and each professional is highly specialized. As a privacy professional, I believe it is my responsibility to advocate for humans whom do not understand they need this support.
Ok, so what is this privacy stuff about? Basically, Privacy is about safeguarding the appropriate use of personal data or Personally Identifiable Information (PII). What about the rest of our information? Should we protect that too?
Some of the most common questions I am asked are things like “How much privacy do I need?” What does the company need to protect? Why do we need so many tools? How much should data protection cost?
These are great questions. In order to effectively answer these questions, it is imperative that you understand the value of data within your organization. Investing in protecting all data equally seems like a phenomenal technique to increase costs and unnecessarily decrease shareholder dividends. The strategic implications for investing in governance, encryption, monitoring and storage (cloud or infrastructure) solutions brings associated expenses to your operating expenses. So, you really need to strategically assess how much and when to invest in the appropriate solution that makes sense for your organization’s needs.
In our current economy, information is being exchanged at exponential rates around the globe. Both consumers and businesses have a ”Data-On-Demand” mentality. Neither segment consciously thinks about the risks associated with each business dealing. For example, when you provide your data to a business in exchange for a product or service what happens next? Does your information stop at the completion of that transaction or is it looped through an infinite network of information exchange downstream? Let’s play this scenario out for a minute to illustrate this point.
Let’s say you are a consumer who loves music. You and a few friends are going to catch a concert at your local stadium. This seems like a simple night, but let’s analyze what happens to your information.
Your first stop is probably going to be to purchase your tickets online using your favorite credit card that doubles points and rewards you with cash back incentives for each purchase. Next you realize you have nothing to wear so you head to the local department store for some retail therapy. After finding the perfect concert apparel you need an energy boost. You decide to order a Starbucks using their app. In the car, you notice that your vehicles gas light indicates you need to stop for fuel. After picking up the cappuccino you swing by the local Costco to maximize your savings on gas prices.
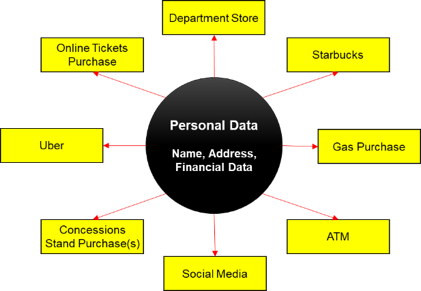
Later that evening your friends all arrive and you guys head to the concert venue. None of you have cash for parking, so you stop at an ATM. Once arriving at the venue, you pay for parking, go through security and are admitted into the stadium. You pass a few concessions stands and decide to purchase refreshments and other items. You make it to your seat but continue purchasing refreshments throughout the evening. At the end of the evening your group decides to leave your car and Uber to an after events. There you decide to upload all of your excitement to social media.
What are the data risks in that scenario? There are at least eight types of data transactions to consider. What security controls does each business have to ensure the security of your data? Do you think the transfer of your data is encrypted? Should you care? Shouldn’t the secure exchange of information be a critical factor for every business. After all, isn’t data their most valuable commodity?
A very important element to any organization is ensuring appropriate safeguards are in place to protect exchanges of personal information. These are vital to preventing fraudulent activity, identity theft, and the confidence of your customers.
Find out why you need machine identity management

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.

