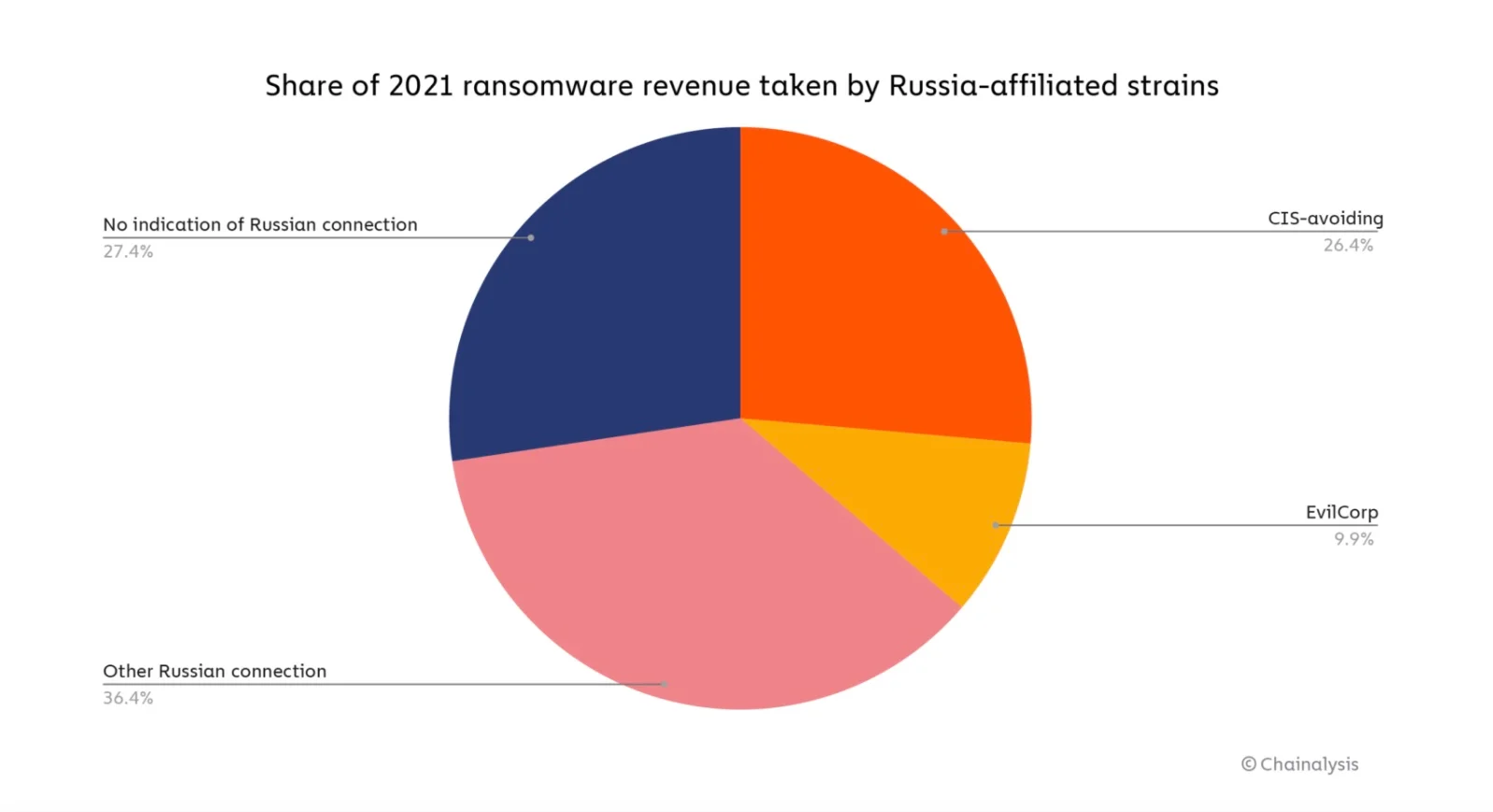
In 2021, roughly 74% of the revenue—over $400 million worth of cryptocurrency—from ransomware went to variants likely linked to Russia, with most of the extorted funds laundered through services primarily catering to Russian users, a new report says. This is happening against a backdrop of Russia’s cyber-destabilization campaigns against Ukraine. These two realities place Russia in the dubious status as a leader in illicit global cyber activity.
Russia’s preeminent position in ransomware is evidenced by a few salient factors, the report from Chainalysis says.
At the top of the list is Evil Corp., a Russia-based purveyor of malware that has become a major force in ransomware. Last year, Evil Corp. launched a new ransomware variant with attackers demanding up to $40 million ransom per attack. And Evil Corp. has nasty reputation that preceded its foray into ransomware. In 2019, Evil Corp malware infected computers and harvested login credentials from hundreds of banks and financial institutions in over 40 countries, causing more than $100 million in theft, as the U.S. Department of Treasury noted when it took legal action against Evil.
Credit: Chainalysis
In a warped interpretation of patriotism, another tell-tale sign of Russian influence is the fact that many major variants are careful to avoid doing damage to Commonwealth of Independent States (CIS), a loose coalition of former Soviet countries.
“Many ransomware strains contain code that prevents the encryption of files if it detects the victim’s operating system is located in a CIS country,” Chainalysis says.
Other indicators of Russia-linked ransomware are variants “that share documents and announcements in the Russian language, or whose affiliates are believed to be located in Russia with a high degree of confidence,” the report said.

SSL/TLS Certificates and Their Prevalence on the Dark Web
Not just ransomware
But it’s not just ransomware. Cryptocurrency-based money laundering and funds associated with other forms of cybercrime go through services with operations in Russia, the report says.
To illustrate this, Chainalysis looked at Cryptocurrency-based money laundering in Moscow City, the capital’s financial district. Specifically, “businesses headquartered or with a significant presence” in Moscow City.
“Collectively, these businesses receive hundreds of millions of dollars’ worth of cryptocurrency per quarter, with totals peaking at nearly $1.2 billion in the second quarter of 2021. In any given quarter, the illicit and risky addresses account for between 29% and 48% of all funds received by Moscow City cryptocurrency businesses. In total, across the three-year period studied, these businesses have received nearly $700 million worth of cryptocurrency from illicit addresses, which represents 13% of all value they’ve received in that time. Where do these illicit funds come from?” (Russian Cybercriminals Drive Significant Ransomware and Cryptocurrency-based Money Laundering Activity, Chainalysis, February 14, 2022)
The report cites seven major businesses receiving large amounts of ransomware funds and cryptocurrency from darknet markets. Those include:
- Garantex: Over $10 million from ransomware strains including NetWalker, Phoenix Cryptolocker, and Conti in the 2019-2021 time period. And a total of $645,223,700 from “illicit and risky cryptocurrency” in the same time period.
- Eggchange: $3,705,827 from illicit and risky cryptocurrency. Chainalysis notes that founder Denis Dubnikov was arrested for his alleged role in helping Ryuk ransomware operators launder funds.
- Buy-bitcoin: $11,374,910 from illicit and risky cryptocurrency. The report notes that Buy-Bitcoin has received $2.1 million from darknet markets, $400,000 in stolen funds, and $400,000 from ransomware attackers.
Russian cyberattacks in Ukraine
Though not necessarily related to the entities and activities cited above, alleged Russian cyberattacks in Ukraine—where a Russian invasion is reported to be imminent—underscore Russia’s status as a center of power for unscrupulous cyberactivity, with ransomware being just one component of a lawless cyber juggernaut.
Cyberattacks in 2015 and 2016 temporarily took down power grids in Ivano-Frankivsk in western Ukraine and Kyiv, the capital, the Wall Street Journal notes in a recent report.
A cyberattack last month, which was blamed on Russia and its ally Belarus, “defaced several dozen government websites and installed malware,” the Journal said, adding that Ukrainian authorities thwarted a more serious attack aimed at the state register, a database of companies and entrepreneurs.
And as a possible Russian invasion of Ukraine looms, a series of cyberattacks this week took down the websites of the Ukrainian army, the defense ministry and major banks offline, Ukrainian authorities said, the AP reported.
Also, Chainalysis and the U.S. Department of Treasury have linked cybercriminal actors, such as Evil Corp., to the Russian government.
Why Do You Need a Control Plane for Machine Identities?
Related posts
- CISA Alert Points to Rise in ‘Sophisticated’ Ransomware Attacks
- What is Ransomware-as-a-Service (RaaS)? Need-to-Know in 2022
- Five Cybersecurity to Pay Attention to in 2022 – Ransomware-as-a-service Is One of the Most Ominous
- Global Security Report: How Are Organizations Reacting to the Rapid Increase in Ransomware Threats

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.

![Russia-Linked Hackers Take Lion’s Share of Ransomware Revenue [Report] - cover graphic](/_next/image/?url=https%3A%2F%2Fcdn.venafi.com%2F994513b8-133f-0003-9fb3-9cbe4b61ffeb%2Fd2c25cf1-afb4-4fd7-8c2f-068f4828e36f%2Faid_field_img__d35464edd6d5a525da982f1aeb8cca3e.jpg%3Fw%3D960%26h%3D540%26fm%3Dwebp%26q%3D85%26fit%3Dcrop&w=3840&q=75&dpl=dpl_CCHxY4sjzWPuuwz2oe2scS3ctPCM)