At the beginning of the year, many organizations were still in the process of moving away from vulnerable SHA-1 certificates. However, despite unsubtle warnings from browsers, detailed distrust schedules and high profile vulnerabilities, we saw prominent organizations still utilizing SHA-1 certificates surprisingly late in the year.
Now, we are facing another high-profile certificate distrust event, one that could be much more disruptive than SHA-1. The downgrading of trust for Symantec certificates will challenge many organizations – especially those who may not realize that some of their digital certificates chain up to Symantec roots.
The expected fallout from Symantec certificates is likely to parallel the SHA-1 scenario in many ways. As we pointed out before, Tom Henderson of Network World published an article regarding SHA-1 certificate failures on April 25th. According to Tom, when he attempted to access a website affiliated with the US government, he was greeted with a SHA-1 warning. This was well after the distrust deadline.
“My case in point is a website that explains the U.S. Safety Act,” wrote Tom. “The Act speaks to the practice of offering legal liability protection for products or services that have been certified for anti-terrorism protection. Any legitimate browser at the moment of this writing will block you from that site and warn you that the chain of authorities needed to vet the site as protected by SSL/TLS does not exist. The site is untrusted.”
Chrome researchers Devon O’Brien, Ryan Sleevi and Andrew Whalley have formally announced the browser’s plan to distrust Symantec’s certificates. The web leader has published a reasonable, but firm, distrust timeline that will hit aggressive milestones all throughout 2018. Other browsers will probably adhere to similar calendars next year.
Unfortunately, if SHA-1 is any indication, it’s highly likely organizations will continue to use distrusted Symantec certificates well after Chrome’s deadlines. Even with the publicity of their timeline.
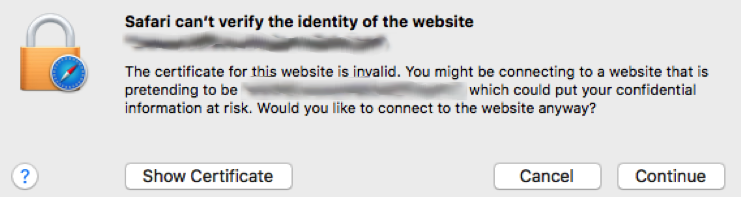
Do you have the agility to replace your Symantec certificates or will your users get warnings like this?
Find out why you need machine identity management

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.

