In a competitive world driven by consumers, companies face the same business challenge: they need to make their data available to their business teams, enabling them to deliver better experiences and to streamline operations. The key to success is to accelerate delivery of trusted data. But this is easier said than done because digital transformation comes with a wide array of technology challenges—from capped IT budgets to lack of resources with the right skillsets, from demanding SLAs to ever-changing technology stacks.
In this three-part blog series, I’ll explore the trends driving the need to evolve management for machine identities in hybrid-cloud environments, security barriers that inhibit machine identities in hybrid clouds and strategies for overcoming these security challenges.

Tale of 3 Clouds eBook: How Venafi Creates Digital Transformation
Let's define hybrid cloud
Before discussing how to manage and protect machine identities in hybrid cloud environments, it is necessary to understand what hybrid cloud is.
Hybrid cloud is a cloud computing environment that uses a mix of on-premise, private cloud and third-party public cloud services with orchestration between the different platforms. By allowing workloads to move between private and public clouds as computing needs and costs change, hybrid cloud gives businesses greater flexibility and more data deployment options.
Cloud offerings have expanded beyond storage and computing to offer a wide array of services. The adoption of other cloud computing models such as Platform as a Service (PaaS), Infrastructure as a Service (IaaS), or Software as a Service, and the growing usage of connected devices and IoT platforms means that additional data and processes are also moving outside of the firewall and into the cloud.
Although cloud computing has become a foundation of digital business, many organizations still struggle to optimize this powerful tool. Cloud computing represents one of the most valuable innovations in current IT and business strategies, but continues to be misunderstood and underutilized. Organizations need to familiarize themselves with the benefits of cloud computing and the associated security risks.
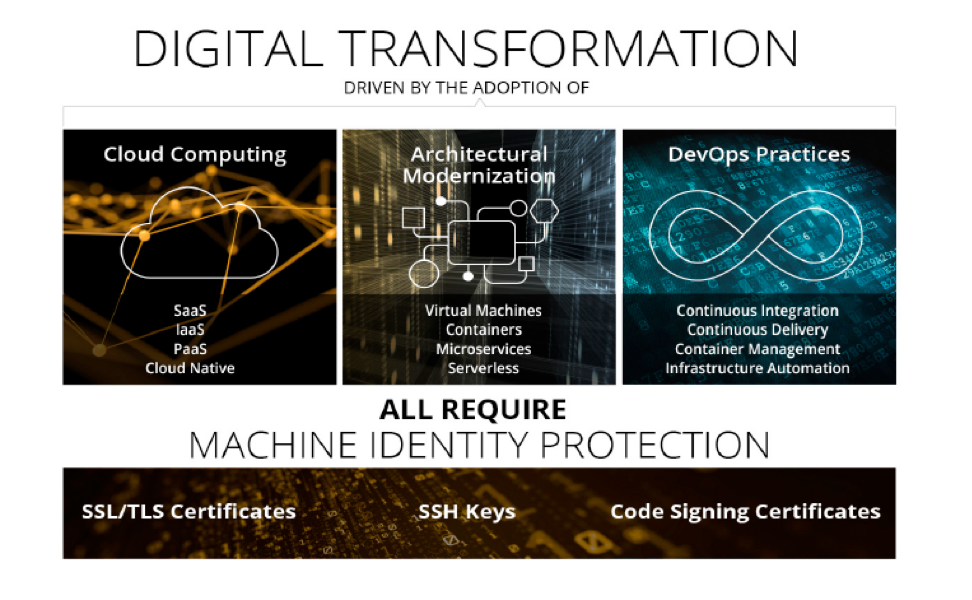
Modernizing the enterprise IT architecture with the cloud is a universal answer to any digital transformation. Microservices architecture is widely used in application modernization as well as digital transformation projects. It is a fresh approach to designing applications as a suite of loosely coupled services that can be developed, deployed, and scaled independently. Microservices-based applications can be easily connected with monolithic applications through APIs and make for a seamless digital transformation. This method helps applications stay agile and future ready.
How does it mix with DevOps?
The latter is tightly coupled with DevOps, which aims at getting high performance and resilient systems at scale. DevOps is really customer-centric and involves a high level of infrastructure automation so as to achieve continuous delivery and integration. DevOps is the combination of cultural philosophies, practices, and tools that enables value to be delivered faster pace than organizations using traditional software development and infrastructure management processes. This speed enables organizations to better serve their customers and compete more effectively in the market.
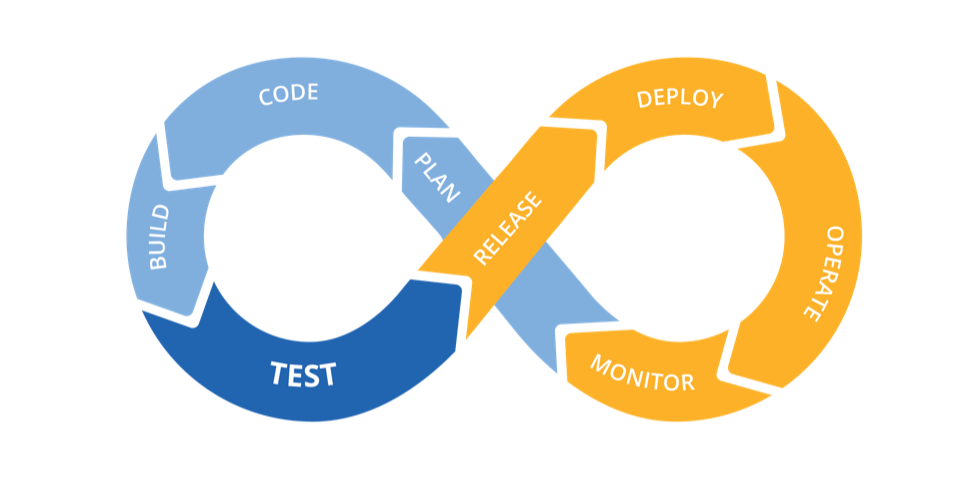
All of the above developments require some form of “hybrid” cloud or multi-cloud. And at the intersection of cloud migration, architecture modernization and DevOps are the machine identities. Certificates are needed across the entire application stack and apply to all infrastructure: servers, containers, cloud services, virtual machines. All communications between machine-to-machine need to be encrypted. In addition, certificates span across the full software lifecycle and need to be embedded within DevOps workflows.
Traditional approaches to machine identities management do not work in the modern enterprise environments. Digital transformation—driven by cloud computing, modern architecture such as containers, VMs, microservices and DevOps practices—requires new approaches to security, demanding the protection of machine identities that enable authentication and encryption required for secure machine-to-machine communication.
In my next post, I’ll discuss in more depth the security challenges that you may face when you build out your machine identity management program for the hybrid cloud.

Machine Identity Management Architecture
Related posts

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.

