OpenSSL has been highly publicized in the last few months—at least for the long standing bugs that have resulted in the complete breakdown of trust in the Internet and the way we do business!
Of the last 6 bugs patched in OpenSSL the most noteworthy are Heartbleed, Cupid, and OpenSSL CCS injection:
- Heartbleed enables an attacker to steal private keys and other sensitive credentials.
- Cupid takes advantage of the Heartbleed flaw in TLS over the Extensible Authentication Protocol (EAP) to attack vulnerable clients connecting to a wireless network or to attack vulnerable wireless access points. The result is similar to that of Heartbleed.
- OpenSSL CCS injection is exploited by an attacker using crafted handshakes to force weak key material to be used between a client and server to perform a man-in-the-middle (MITM) attack.
It would seem from the recent examples that attackers are more brazenly using SSL / TLS against organizations with great success. We need to ask ourselves why. I believe we can answer this question by simply reviewing the response that most organizations have taken to remediate Heartbleed and evaluate where they are now.
Venafi Labs frequently analyzes the websites of the Global 2000 organizations and the Alexa Top 1 Million to identify SSL / TLS vulnerabilities. We have found that although many organizations believe they are not susceptible to Heartbleed anymore, the data shows otherwise.
As part of our analysis for Heartbleed we first compared scanning results with previously published Heartbleed vulnerable lists from ZMAP and Github. It was pleasant to see that most domains listed on these repositories have remediated correctly. However, there are a large number of organizations that are not included on the lists and are still vulnerable. Our scan data specifically focuses on Global 2000 organizations to better understand how successful they have been at remediating Heartbleed.
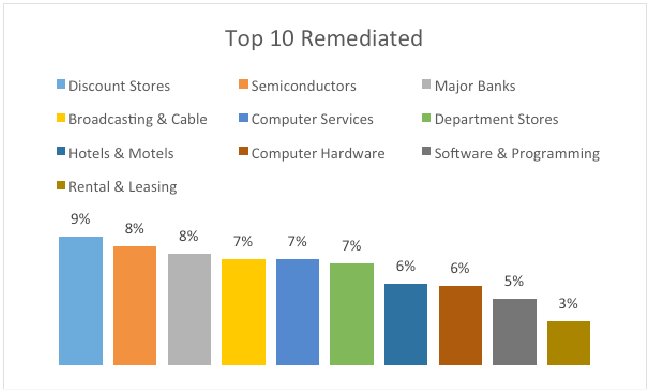
Even though most Global 2000 organizations have taken steps to remediate Heartbleed, many have not fully remediated. When comparing the organizations that have correctly remediated, it would seem that discount stores took the Target breach to heart. They account for 9% that achieved full remediation of systems from the sample set.
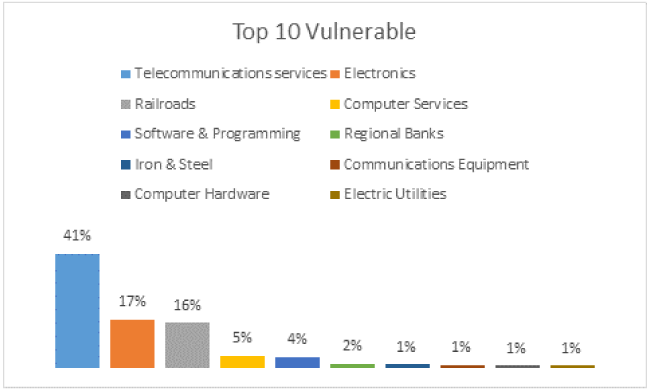
On the other hand, telecommunications services have a long way to go to remediate Heartbleed. They are responsible for 41% of the confirmed Heartbleed vulnerable systems from the Global 2000 scan. Think of the wealth of information that cybercriminals are still syphoning off these vulnerable systems from Telecommunications services’ customers!
Heartbleed has been known to the world for 10 weeks now. Yet we still see evidence of thousands of systems susceptible to Heartbleed that have not even been patched yet. Venafi Labs will periodically publish updated information on organizations’ effectiveness with remediating the Heartbleed vulnerability based on our analysis of trust-based attacks.
Learn how Venafi can help identify systems susceptible to Heartbleed and the required remediation.
Why Do You Need a Control Plane for Machine Identities?

2024 Machine Identity Management Summit
Help us forge a new era of cybersecurity
Looking to vulcanize your security with an identity-first strategy? Register today and save up to $100 with exclusive deals. But hurry, this sale won't last!

